Podcast (behind-the-woodshed): Play in new window | Download (Duration: 1:59:45 — 18.2MB) | Embed
BTWRLM207
Behind The Woodshed 3rd year Anniversary at Real Liberty Media
At the Situationally Aware Action Oriented Intelligence Center
Of Evolutionary Engagement

The Victory Against You in the Silent War is Your Silence
Wallowing Wounded
Engaging in counter-propaganda tactics and related work
Human-Spinach Hybrid: Plant People – Soylent Green
- Spinach Leaf Transformed Into Beating Human Heart Tissue
Using the plant like scaffolding, scientists built a mini version of a working heart, which may one day aid in tissue regeneration.
Their study, published this month by the journal Biomaterials, offers a new way to grow a vascular system, which has been a roadblock for tissue engineering.
Scientists have already created large-scale human tissue in a lab using methods like 3D printing, but it’s been much harder to grow the small, delicate blood vessels that are vital to tissue health.
“The main limiting factor for tissue engineering … is the lack of a vascular network,” says study co-author Joshua Gershlak, a graduate student at Worcester Polytechnic Institute (WPI) in Massachusetts, in a video describing the study. “Without that vascular network, you get a lot of tissue death.”
One of the defining traits of a leaf is the branching network of thin veins that delivers water and nutrients to its cells. Now, scientists have used plant veins to replicate the way blood moves through human tissue. The work involves modifying a spinach leaf in the lab to remove its plant cells, which leaves behind a frame made of cellulose.
“Cellulose is biocompatible [and] has been used in a wide variety of regenerative medicine applications, such as cartilage tissue engineering, bone tissue engineering, and wound healing,” the authors write in their paper.
Pharma Harma
- Pivotal Lawsuit Shows Widely Used Antidepressant Increases Suicide Risk Over 800 Percent
A trial is currently underway in Illinois as a widow seeks to hold pharmaceutical manufacturer GlaxoSmithKline accountable for improper labeling and minimizing a potentially serious side effect of a well-known antidepressant.
Paroxetine is a widely prescribed antidepressant and anti-anxiety drug under the class of drugs known as selective serotonin reuptake inhibitors (SSRIs). Paroxetine is most commonly known as the brand name of Paxil, manufactured by GlaxoSmithKline (GSK).
Since 2012, Wendy Dolin has been engaged in a legal battle against GSK following the suicide of her husband, Stewart Dolin. Wendy says that in the summer of 2010, Stewart was prescribed a generic version of Paxil for anxiety issues related to work. According to Wendy, Stewart Dolin complained of becoming increasingly anxious and restless and was unable to sleep while taking the drug. On July 15, 2010, less than one week after beginning this medication, Stewart committed suicide by walking in front of a train.
Wendy began searching for answers in the wake of her husband’s suicide and said she learned that he had been displaying signs of akathisia, a disorder characterized by an individual’s inability to relax or sit still. Psychiatrist Joseph Glenmullen said in 2006 that “Patients have described [akathisia] to me as listening to nails scratching on a black board 24/7, or your bones rattling like tuning forks. It is this inner agitation that is by far the most dangerous.” In 2012, Wendy filed a legal complaint against GSK seeking to hold the manufacturer liable for her husband’s death. The complaint noted that “a scientist working for another SSRI manufacturer, Pfizer, wrote in a 1998 medical journal article that the suicidal impulses resulting from akathisia may be explained as a feeling that ‘death is a welcome result’ when the ‘acutely discomforting symptoms of akathisia are experienced on top of already distressing disorders.’”
The critical issue in Wendy Dolin’s lawsuit is not simply paroxetine itself. It’s no secret that lawsuits against pharmaceutical companies are usually complicated under most circumstances, but this case is particularly notable as a tragic example of the gray area of liability when a patient is prescribed a generic drug, as well as the problems between the FDA and drugmakers that exist when it comes to publishing safety labels for patients and doctors.
- Infant mortality rates regressed against number of vaccine doses routinely given: Is there a biochemical or synergistic toxicity?
Abstract
The infant mortality rate (IMR) is one of the most important indicators of the socio-economic well-being and public health conditions of a country. The US childhood immunization schedule specifies 26 vaccine doses for infants aged less than 1 year—the most in the world—yet 33 nations have lower IMRs. Using linear regression, the immunization schedules of these 34 nations were examined and a correlation coefficient of r = 0.70 (p < 0.0001) was found between IMRs and the number of vaccine doses routinely given to infants. Nations were also grouped into five different vaccine dose ranges: 12–14, 15–17, 18–20, 21–23, and 24–26. The mean IMRs of all nations within each group were then calculated. Linear regression analysis of unweighted mean IMRs showed a high statistically significant correlation between increasing number of vaccine doses and increasing infant mortality rates, with r = 0.992 (p = 0.0009). Using the Tukey-Kramer test, statistically significant differences in mean IMRs were found between nations giving 12–14 vaccine doses and those giving 21–23, and 24–26 doses. A closer inspection of correlations between vaccine doses, biochemical or synergistic toxicity, and IMRs is essential.
Keywords: infant mortality rates, sudden infant death, SIDS, immunization schedules, childhood vaccines, drug toxicology, synergistic effects, linear regression model, - Zika vaccine: watch out—it will alter your DNA
First, I’ll lay out a little background—
In many previous articles, I’ve established there is no convincing evidence the Zika virus causes the birth defect called microcephaly. (Zika archive here)
Basically, Brazilian researchers, in the heart of the purported “microcephaly epidemic,” decided to stop their own investigation and simply assert Zika was the culprit. At that point, they claimed that, out of 854 cases of microcephaly, only 97 showed “some relationship” to Zika.
You need to understand that these figures actually show evidence AGAINST Zika. When researchers are trying to find the cause of a condition, they should be able to establish, as a first step, that the cause is present in all cases (or certainly an overwhelming percentage).
This never happened. The correlation between the presence of Zika and microcephaly was very, very weak.
As a second vital step, researchers should be able to show that the causative virus is, in every case, present in large amounts in the body. Otherwise, there is not enough of it to create harm. MERE PRESENCE OF THE VIRUS IS NOT ENOUGH. With Zika, proof it was present in microcephaly-babies in large amounts has never been shown.
All this fraud set the stage for the Zika DNA vaccine. Yes, it is under development. It is, in fact, an example of the next generation of vaccines. And this is why you should watch out.
Here is an excerpt from a US National Institutes of Health press release (8/3/16) (here, here, and, the booster to the DNA vaccine here):
“The National Institute of Allergy and Infectious Diseases (NIAID), part of the National Institutes of Health [NIH], has launched a clinical trial of a vaccine candidate intended to prevent Zika virus infection.”
“Scientists at NIAID’s Vaccine Research Center (VRC) developed the investigational vaccine — called the NIAID Zika virus investigational DNA vaccine — earlier this year.”
“The investigational Zika vaccine includes a small, circular piece of DNA — called a plasmid — that scientists engineered to contain genes that code for proteins of the Zika virus. When the vaccine is injected into the arm muscle, cells [in the person’s body] read the genes and make Zika virus proteins, which self-assemble into virus-like particles. The body mounts an immune response to these particles, including neutralizing antibodies and T cells. DNA vaccines do not contain infectious material — so they cannot cause a vaccinated individual to become infected with Zika — and have been shown to be safe in previous clinical trials for other diseases.”
SYNTHESIZED GENES ARE INJECTED INTO THE BODY.
That’s why it’s called a DNA vaccine.
Beginning to wonder what this is all about?
It’s about PERMANENTLY ALTERING YOUR DNA.
It’s about altering the DNA of every person on the planet who is vaccinated.
New York Times, 3/9/15, “Protection Without a Vaccine.” The article describes the frontier of research. Here are key quotes that illustrate the use of synthetic genes to “protect against disease,” while changing the genetic makeup of humans. This is not science fiction:
“By delivering synthetic genes into the muscles of the [experimental] monkeys, the scientists are essentially re-engineering the animals to resist disease.”
“’The sky’s the limit,’ said Michael Farzan, an immunologist at Scripps and lead author of the new study.”
“The first human trial based on this strategy — called immunoprophylaxis by gene transfer, or I.G.T. — is underway, and several new ones are planned.” [That was nearly two years ago.]
“I.G.T. is altogether different from traditional vaccination. It is instead a form of gene therapy. Scientists isolate the genes that produce powerful antibodies against certain diseases and then synthesize artificial versions. The genes are placed into viruses and injected into human tissue, usually muscle.”
Here is the punchline: “The viruses invade human cells with their DNA payloads, and the synthetic gene is incorporated into the recipient’s own DNA. If all goes well, the new genes instruct the cells to begin manufacturing powerful antibodies.”
Read that again: “the synthetic gene is incorporated into the recipient’s own DNA.”
Alteration of the human genetic makeup.
Diversity Agenda Leads To
- College ‘Diversity Council’ Admits to Posting Fake Racist Flyers On Campus
The idea was to encourage ‘dialogue.’
The Diversity Leadership Council at Gustavus Adolphus College admits that it — with the help of other social-justice groups — planted fake racist flyers on campus “to educate” people about racism.
The flyers, according to a photo obtained by Campus Reform, stated:
A NOTICE
TO ALL WHITE AMERICANS
IT IS YOUR CIVIC DUTY
TO REPORT ANY AND ALL ILLEGAL ALIENS
TO U.S. IMMIGRATION AND CUSTOMS ENFORCEMENT
THEY ARE CRIMINALS
AMERICA IS A WHITE NATION
Obviously, these flyers caused a huge uproar among the school’s students and alumni — only for Dean of Students Jones VanHecke to later announce that they were “part of a series of educational ‘invisible theater’ events taking place this week that have been planned by I Am We Are theater troupe, the Diversity Leadership Team, and the Bystander Intervention Committee.”
“We want to help put an end to bias-related incidents that happen on our campus, social media, and in our communities by forcing individuals to have dialogues about forms of hate and bias,” the post stated.
Hey, kids? If you want to “help put an end to bias-related incidents that happen on our campus,” how about you address those incidents instead of distracting from them by making up a fake one? Seriously — just what is bringing awareness to a fake issue going to solve? It’s not going to help solve that issue, because — and sorry if I’m blowing your mind here — a problem has to actually exist in order for you to be able to solve it.
- Israeli-American Teen Arrested for Making Jewish Center Bomb Threats Worldwide
A 19-year-old American-Israeli student was arrested Thursday on charges that he was behind the majority of threats called into Jewish centers, synagogues and schools in the US, Europe, Australia and New Zealand over the past six months. Additionally, the man’s father has been ordered to be detained for eight days on suspicion that he knew about or also called in many of the threats. He denies any involvement in or knowledge of his son’s actions.
A lawyer for the teen, who was apprehended in Ashkelon in southern Israel, has claimed that his behavior is related to a brain tumor, which caused him to be rejected by the Israeli Defense Force.
“He suffers from a brain tumor that may have had an effect on his cognitive functions,” his lawyer, Galit Bash, said in a statement released by the Office of the Israeli Public Defender.
The investigation was complicated, as the teen, who has not yet been named, was using “advanced camouflage technologies” to hide his identity. It has been confirmed that he holds both American and Israeli citizenship.
What’s Inside? Intel
- Vault 7: Projects – Dark Matter
Today, March 23rd 2017, WikiLeaks releases Vault 7 “Dark Matter”, which contains documentation for several CIA projects that infect Apple Mac firmware (meaning the infection persists even if the operating system is re-installed) developed by the CIA’s Embedded Development Branch (EDB). These documents explain the techniques used by CIA to gain ‘persistence’ on Apple Mac devices, including Macs and iPhones and demonstrate their use of EFI/UEFI and firmware malware.
Among others, these documents reveal the “Sonic Screwdriver” project which, as explained by the CIA, is a “mechanism for executing code on peripheral devices while a Mac laptop or desktop is booting” allowing an attacker to boot its attack software for example from a USB stick “even when a firmware password is enabled”. The CIA’s “Sonic Screwdriver” infector is stored on the modified firmware of an Apple Thunderbolt-to-Ethernet adapter.
“DarkSeaSkies” is “an implant that persists in the EFI firmware of an Apple MacBook Air computer” and consists of “DarkMatter”, “SeaPea” and “NightSkies”, respectively EFI, kernel-space and user-space implants.
Documents on the “Triton” MacOSX malware, its infector “Dark Mallet” and its EFI-persistent version “DerStarke” are also included in this release. While the DerStarke1.4 manual released today dates to 2013, other Vault 7 documents show that as of 2016 the CIA continues to rely on and update these systems and is working on the production of DerStarke2.0.
Also included in this release is the manual for the CIA’s “NightSkies 1.2” a “beacon/loader/implant tool” for the Apple iPhone. Noteworthy is that NightSkies had reached 1.2 by 2008, and is expressly designed to be physically installed onto factory fresh iPhones. i.e the CIA has been infecting the iPhone supply chain of its targets since at least 2008.
While CIA assets are sometimes used to physically infect systems in the custody of a target it is likely that many CIA physical access attacks have infected the targeted organization’s supply chain including by interdicting mail orders and other shipments (opening, infecting, and resending) leaving the United States or otherwise.
- WikiLeaks Vault 7 Leak Claims CIA Bugs ‘Factory Fresh’ iPhones
A new WikiLeaks Vault 7 leak titled “Dark Matter” claims, with unreleased documents, that the Central Intelligence Agency has been bugging “factory fresh” iPhones since at least 2008. WikiLeaks further claims that the CIA has the capability to permanently bug iPhones, even if their operating systems are deleted or replaced.
The documents are expected to be released in the next 24-hours. The announced was made after a “press briefing” that WikiLeaks promoted on its Twitter.
- Glenn Greenwald: how the NSA tampers with US-made internet routers
The NSA has been covertly implanting interception tools in US servers heading overseas – even though the US government has warned against using Chinese technology for the same reasons, says Glenn Greenwald, in an extract from his new book about the Snowden affair, No Place to Hide
• The explosive day we revealed Edward Snowden’s identity
• The state targets dissenters not just ‘bad guys’
• Glenn Greenwald: ‘I don’t trust the UK not to arrest me’For years, the US government loudly warned the world that Chinese routers and other internet devices pose a “threat” because they are built with backdoor surveillance functionality that gives the Chinese government the ability to spy on anyone using them. Yet what the NSA’s documents show is that Americans have been engaged in precisely the activity that the US accused the Chinese of doing.
The drumbeat of American accusations against Chinese internet device manufacturers was unrelenting. In 2012, for example, a report from the House Intelligence Committee, headed by Mike Rogers, claimed that Huawei and ZTE, the top two Chinese telecommunications equipment companies, “may be violating United States laws” and have “not followed United States legal obligations or international standards of business behaviour”. The committee recommended that “the United States should view with suspicion the continued penetration of the US telecommunications market by Chinese telecommunications companies”.
The Rogers committee voiced fears that the two companies were enabling Chinese state surveillance, although it acknowledged that it had obtained no actual evidence that the firms had implanted their routers and other systems with surveillance devices. Nonetheless, it cited the failure of those companies to cooperate and urged US firms to avoid purchasing their products: “Private-sector entities in the United States are strongly encouraged to consider the long-term security risks associated with doing business with either ZTE or Huawei for equipment or services. US network providers and systems developers are strongly encouraged to seek other vendors for their projects. Based on available classified and unclassified information, Huawei and ZTE cannot be trusted to be free of foreign state influence and thus pose a security threat to the United States and to our systems.”
The constant accusations became such a burden that Ren Zhengfei, the 69-year-old founder and CEO of Huawei, announced in November 2013 that the company was abandoning the US market. As Foreign Policy reported, Zhengfei told a French newspaper: “‘If Huawei gets in the middle of US-China relations,’ and causes problems, ‘it’s not worth it’.”
But while American companies were being warned away from supposedly untrustworthy Chinese routers, foreign organisations would have been well advised to beware of American-made ones. A June 2010 report from the head of the NSA’s Access and Target Development department is shockingly explicit. The NSA routinely receives – or intercepts – routers, servers and other computer network devices being exported from the US before they are delivered to the international customers.
The agency then implants backdoor surveillance tools, repackages the devices with a factory seal and sends them on. The NSA thus gains access to entire networks and all their users. The document gleefully observes that some “SIGINT tradecraft … is very hands-on (literally!)”.
Eventually, the implanted device connects back to the NSA. The report continues: “In one recent case, after several months a beacon implanted through supply-chain interdiction called back to the NSA covert infrastructure. This call back provided us access to further exploit the device and survey the network.”
Windows IS Malware
- Security Alert: Windows 10 Has Been Quietly Logging EVERY KEYSTROKE You Type And Sending It To Microsoft (This Is How To Stop It)
Yesterday we reported that an international group of hackers claim they have breached Apple’s iCloud user database and stolen 300 million usernames and passwords. The group has threatened to initiate a widespread factory reset on April 7th, 2017, potentially wiping out data on tens of millions of iPhones and iCloud accounts should Apple fail to pay a ransom.
But that breach by nefarious hackers, while serious, is nothing compared to what your trusted operating system provider may be doing on your personal computer.
According to a recent report, if you are a Windows 10 user then every single keystroke you have ever typed on your computer may have been logged and sent to Microsoft.
You know those nagging questions during the installation process that ask you whether or not you want to “help” improve Windows by sending data to Microsoft? If you happened to answer “yes” to one of these questions, or if you went with the Microsoft default installation, there is a real possibility that everything you have done on your computer from the get-go, including sending “secure” messages (because the keyboard logger captures your keystrokes before they appear in your secure messaging app), is now a part of a massive user database somewhere.
There’s been heaps of controversy associated with Microsoft’s latest operating system Windows 10 since it was launched, but the latest issue takes the cake – apparently Windows has been quietly logging every single keystroke users make on their keyboards from the beginning. Even better, that data is being constantly sent to Microsoft’s servers on a regular basis.
Via IB Times
It’s been reported that Microsoft has been using the data to improve artificial intelligence writing and grammar software, but it’s not clear what else they are doing with it.
- Windows 10 keylogger: How to stop Microsoft from tracking everything you type
There’s been heaps of controversy associated with Microsoft’s latest operating system Windows 10 since it was launched, but the latest issue takes the cake – apparently Windows has been quietly logging every single keystroke users make on their keyboards from the beginning. Even better, that data is being constantly sent to Microsoft’s servers on a regular basis.
We’re not sure why on earth Microsoft would want users’ keystrokes, as this data is only really useful to cybercriminals seeking to crack passwords to steal sensitive data, and IBTimes UK has asked the computing giant to clarify, but in the meantime, it is possible to solve this problem.
Here’s advice on how to turn off the Windows 10 keylogger:
Concerned about privacy? Then always say no
If you haven’t yet installed Windows 10 but are thinking of upgrading, then your road ahead is simple. When you install Windows 10, make sure that you select ‘custom install’.
Read all the options on the installation window carefully, and make sure you always select ‘no’ for all options relating to sending data to Microsoft. It is also safe if you simply choose to just say ‘no’ to all options – it will not affect your usability on Windows 10.
I have Windows 10. What should I do?
If you have Windows 10 installed, then you need to go to the Start menu and then select Settings > Privacy > General. Turn off the option that reads, ‘Send Microsoft info about how I write to help us improve typing and writing in the future’. To be safe, restart your computer after selecting this option.
I have technical knowledge. Is there anything else I can do?
Yes, there are several things you can do to prevent being tracked. The problem is that even if you turn tracking options off, if in the future Microsoft decides that it wants the options to be turned back on for any reason, it can easily do so during the monthly Patch Tuesday through the automatic Windows Updates function.
There are ways that you can prevent this from happening, however, please be aware that these methods come from the user community, and some of these fixes could potentially cause problems to your PC. We’ve listed possible options ranked from “harmless” to “most likely to mess up your computer”.
Swamp Surveillance Stamp of Approval
- Senate votes to kill privacy rules guarding your online info
The Senate voted to kill Obama-era online privacy regulations, a first step toward allowing internet providers such as Comcast, AT&T and Verizon to sell your browsing habits and other personal information as they expand their own online ad businesses.
Those rules, not yet in effect, would have required internet providers to ask your permission before sharing your personal information. That’s a much stronger privacy-protection weapon than letting them use your data until you tell them to stop. As anyone who has ever tried to stop getting targeted ads on the internet knows, opting out is hard.
Without those protections, consumer advocates fear that broadband providers will be able to do what they like with people’s data.
“Advertisers and marketers are lining up to get access to all the information that’s now available about us,” said Jeff Chester of the Center for Digital Democracy, which advocates for tougher internet privacy measures.
Supreme Disapproval
- Supreme Court rules cell phones cannot be searched without a warrant
Police need a warrant to search the cell phone of a person who has been arrested, absent special circumstances, a unanimous Supreme Court ruled Wednesday.
“Modern cell phones are not just another technological convenience. With all they contain and all they may reveal, they hold for many Americans ‘the privacies of life,’” Chief Justice John Roberts wrote. “The fact that technology now allows an individual to carry such information in his hand does not make the information any less worthy of the protection for which the Founders fought. Our answer to the question of what police must do before searching a cell phone seized incident to an arrest is accordingly simple — get a warrant.”
The high court took two cases involving cell phone searches, one involving a smartphone and the other involving a relatively basic flip phone. In both cases, police used information on each phone to connect the plaintiffs to crimes. San Diego Police used pictures in David Leon Riley’s smartphone, and the guns they found in his trunk after pulling him over for a traffic violation, to tie him to a local faction of the Bloods street gang and an earlier shooting. In Boston, Brima Wurie was arrested on suspicion of being involved in selling drugs and a picture linked to a phone call on his flip phone to a stash of crack cocaine.
The decision will likely have long-lasting implications for digital privacy, far beyond the immediate concern surrounding how and when police can search a mobile device. Police are typically allowed to search an individual after an arrest, but Roberts wrote that the amount of personal information contained on a cell phone made such a search different from the usual objects authorities might find when asking someone to empty their pockets.
“A cell phone search would typically expose to the government far more than the most exhaustive search of a house,” he wrote. “A phone not only contains in digital form many sensitive records previously found in the home; it also contains a broad array of private information never found in a home in any form—unless the phone is.”
The court held that the “exigent circumstances” exception to the warrant requirement also applied to cell phones – that is, imminent danger to life or the possibility that evidence would be destroyed might justify searching a phone without a warrant. Justice Samuel Alito, in a concurrence, opened the door to further exceptions. Alito wrote that he would “reconsider the question presented here if either Congress or state legislatures, after assessing the legitimate needs of law enforcement and the privacy interests of cell phone owners, enact legislation that draws reasonable distinctions based on categories of information or perhaps other variables.”
Your Defenseless Future?
- Appeals Court Says Prior Restraint Is Perfectly Fine, Refuses To Rehear 3D-Printed Guns Case
It looks as though the Supreme Court may have to step in and settle a particularly thorny question involving the First Amendment, Second Amendment, national security interests, and 3D-printed weapons. Cody Wilson and his company, Defense Distributed, sued the State Department over its demands he cease distributing instructions for the creation of weapons and weapons parts.
The State Department came along too late to make much of a difference. It claimed Wilson’s instructions violated international arms distribution laws, but by the time it noticed what Defense Distributed was doing, the instructions were all over the web. They still are, and no amount of litigation or government orders is going to change that.
What Defense Distributed is doing is perfectly legal in the United States. The State Department says it’s illegal to put these instructions in the hands of foreign enemies. Since it can’t control internet traffic, it’s decided to take down the publisher.
That’s the First Amendment implication, which can’t really be separated from Second Amendment concerns considering the legality of distributing these instructions domestically. Last September, the Fifth Circuit Appeals Court found [PDF] in favor of the government and its national security concerns.
Because both public interests asserted here are strong, we find it most helpful to focus on the balance of harm requirement, which looks to the relative harm to both parties if the injunction is granted or denied. If we affirm the district court’s denial, but Plaintiffs-Appellants eventually prove they are entitled to a permanent injunction, their constitutional rights will have been violated in the meantime, but only temporarily. Plaintiffs-Appellants argue that this result is absurd because the Published Files are already available through third party websites such as the Pirate Bay, but granting the preliminary injunction sought by Plaintiffs-Appellants would allow them to share online not only the Published Files but also any new, previously unpublished files. That leads us to the other side of the balance of harm inquiry.
If we reverse the district court’s denial and instead grant the preliminary injunction, Plaintiffs-Appellants would legally be permitted to post on the internet as many 3D printing and CNC milling files as they wish, including the Ghost Gunner CNC milling files for producing AR-15 lower receivers and additional 3D-printed weapons and weapon parts. Even if Plaintiffs-Appellants eventually fail to obtain a permanent injunction, the files posted in the interim would remain online essentially forever, hosted by foreign websites such as the Pirate Bay and freely available worldwide. That is not a far-fetched hypothetical: the initial Published Files are still available on such sites, and Plaintiffs-Appellants have indicated they will share additional, previously unreleased files as soon as they are permitted to do so. Because those files would never go away, a preliminary injunction would function, in effect, as a permanent injunction as to all files released in the interim. Thus, the national defense and national security interest would be harmed forever. The fact that national security might be permanently harmed while Plaintiffs-Appellants’ constitutional rights might be temporarily harmed strongly supports our conclusion that the district court did not abuse its discretion in weighing the balance in favor of national defense and national security.
A lengthy dissent challenged the First Amendment implications of this decision, which brought prior restraint into play by forbidding Defense Distributed from posting new instructions, along with further distribution of plans it had already released. But the majority didn’t find much it liked in the dissent — at least not when weighing it against the government’s national security interests.
The dissent argues that we “should have held that the domestic internet publication” of the technical data at issue presents no “immediate danger to national security, especially in light of the fact that many of these files are now widely available over the Internet and that the world is awash with small arms.” We note the following:
(1) If Plaintiffs-Appellants’ publication on the Internet were truly domestic, i.e., limited to United States citizens, there is no question that it would be legal. The question presented in this case is whether Plaintiffs-Appellants may place such files on the Internet for unrestricted worldwide download.
(2) This case does not concern only the files that Plaintiffs-Appellants previously made available online. Plaintiffs-Appellants have indicated their intent to make many more files available for download as soon as they are legally allowed to do so. Thus, the bulk of the potential harm has not yet been done but could be if Plaintiffs-Appellants obtain a preliminary injunction that is later determined to have been erroneously granted.
(3) The world may be “awash with small arms,” but it is not yet awash with the ability to make untraceable firearms anywhere with virtually no technical skill. For these reasons and the ones we set out above, we remain convinced that the potential permanent harm to the State Department’s strong national security interest outweighs the potential temporary harm to Plaintiffs-Appellants’ strong First Amendment interest.
The majority also pointed out the government can violate the First Amendment in the interest of national security, and that this court in particular seemed inclined to let it.
Defense Distributed asked for an en banc rehearing. That has been denied [PDF]. This denial gives the dissent the chance to lead off (so to speak), and the first thing it does is point out the obvious First Amendment violations.
The panel opinion’s flawed preliminary injunction analysis permits perhaps the most egregious deprivation of First Amendment rights possible: a content-based prior restraint. […] First, the panel opinion fails to review the likelihood of success on the merits—which ten of our sister circuits agree is an essential inquiry in a First Amendment preliminary injunction case. Second, the panel opinion accepts that a mere assertion of a national security interest is a sufficient justification for a prior restraint on speech. Third, the panel opinion conducts a fundamentally flawed analysis of irreparable harm.
As the dissent points out, the majority chose to deploy prior restraint based on little more than the government’s vague claims of insecurity.
The Government contends that the gun designs at issue could potentially threaten national security. However, this speculation falls far short of the required showing under Bernard and Nebraska Press, showing neither the immediacy of the danger nor the necessity of the prior restraint. Allowing such a paltry assertion of national security interests to justify a grave deprivation of First Amendment rights treats the words “national security” as a magic spell, the mere invocation of which makes free speech instantly disappear.
But this is exactly what the government does: make rights disappear with its “magic spell.” And the courts continue to let it do this. In this case alone, the invocation of “national security” resulted in three consecutive decisions (district court and twice at the appeals court) in favor of prior restraint.
- Cops given pass for shooting innocent man in his own apartment
There was no warrant and no reason to suspect the apartment resident in Lake County, Florida, of a crime. But police officers who said they were investigating a speeding motorcyclist, to which the man had no links, pounded on the door at 1:30 in the morning.
When Andrew Scott, 26, answered the door, carrying a weapon for defense because of the vigorous knocking at an unlikely hour, an officer shot and killed him.
Now, the 11th U.S. Circuit Court of Appeals has given the officer a pass for the killing, prompting an outraged dissent from four justices on the panel.
The judges contend the outcome “makes it more likely that tragic police shootings will continue to occur.”
The warning, written by Justice Beverly Martin and joined by Charles Wilson, Robin Rosenbaum and Jill Pryor, said: “Andrew Scott and his girlfriend were in their home playing video games late one night when police arrived outside. The police had no warrant and no reason to suspect Mr. Scott or his girlfriend had committed any crime. The officers acknowledge both of these things to be true.
“Even so, the police tactically surrounded the home’s only exit, drew their guns, repeatedly slammed on the door without identifying themselves as law enforcement, and then shot and killed Scott when he opened the door, as he was stepping back into his home,” they wrote.
The four judges found problems with the majority’s ruling that the police officers’ actions were justified.
- Lawsuit: Police Destroyed Farm House To Capture Homeless Man Armed With An Ice Cream Bar
from the USE-ALL-THE-TOYS!!! dept
Is it possible to arrest an unarmed homeless person without destroying the residence he’s hiding in? To the Fresno County Sheriff’s Department and Clovis PD (and far too many other law enforcement agencies), the question remains rhetorical.
David Jessen’s farmhouse felt the full, combined force of two law enforcement agencies and all their toys last June. According to his lawsuit [PDF], a homeless man was rousted from a nearby vacant house after he was discovered sleeping in the closet. He left peacefully but was soon spotted by the construction crew breaking into Jessen’s house. The construction worker, god bless him, called the police because he thought they could help.
Jessen was notified shortly thereafter. He returned home to find four sheriff’s office cars parked at his residence (one of them “on the lawn,” because of course it was) and a deputy yelling at his house through a bullhorn. According to the deputies, the homeless man refused to come out and threatened to shoot anyone who came in. Jessen was asked if he had any guns in the house. He replied he did, but two were unloaded and had no ammo and the third was hidden so well “only he could find it.”
Jessen was asked to move his pickup truck and leave the area for his own safety. The deputies also asked for a house key and for the garage to be opened before he left. Jessen and his family went to a friend’s house about a quarter-mile away. Several hours later, he was told he could return home. This is what Jessen returned to:
As David was driving toward the home from Jensen David counted approximately fifty-five (55) or more law enforcement vehicles. David was then ordered to park along Rolinda Avenue north of his home and instructed to walk to his home. On his way to his home David was stopped by a SWAT person who told him the “operation” was concluded, A second Fresno County Deputy Sheriff, that Jessen’s are informed and believe and upon information and belief allege was a Lieutenant, handed David a card and said “we have insurance for this.”
We’ll pause there for a moment and consider the effect this must have on recipients. This is basically a message telling them their stuff has been damaged/destroyed. Not that the law enforcement agency cares. It might end up with higher premiums, but each officer involved still has an undamaged residence to go home to, unlike “civilians” like Jessen, whose houses happen to be at the wrong place at the wrong time. Insurance in the hands of officers like these is a permission slip, rather than a liability buffer.
Continuing on…
MonSatan Chemical Consequences
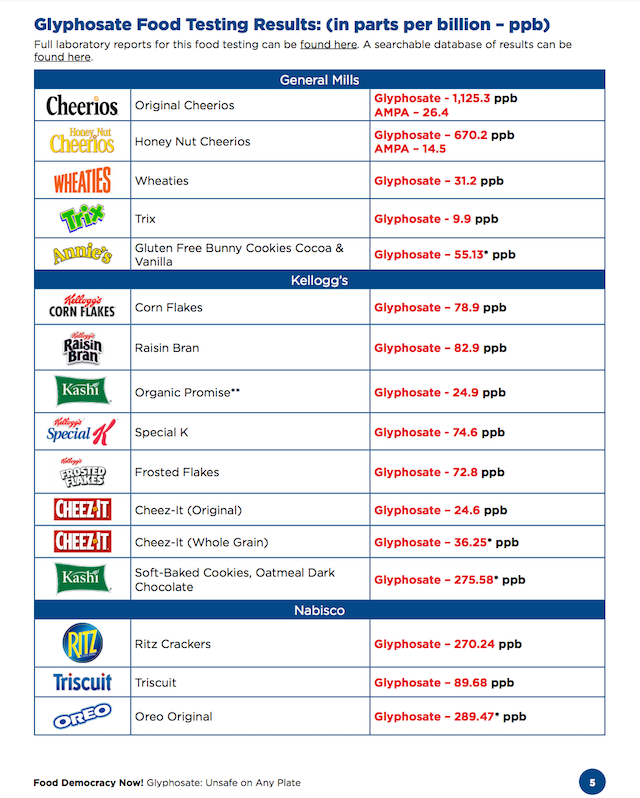
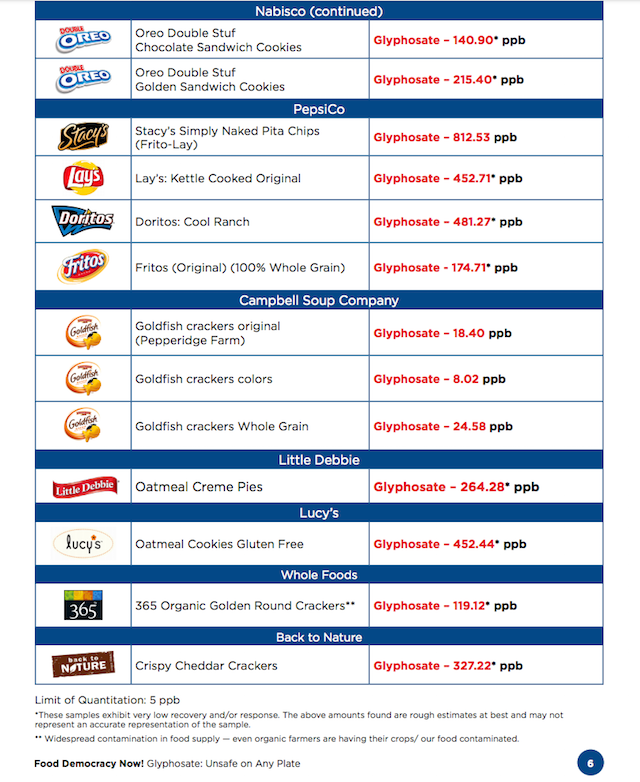
- Monsanto Is Scrambling To Bury This Breaking Story – Don’t Let This Go Unshared!
PLEASE SHARE this with all your friends! We mustn’t keep quiet about the evils about Monsanto!

Share this shocking new report with everyone you know….
A FDA-registered food safety laboratory tested iconic American food for residues of the weed killer glyphosate (aka Monsanto’s Roundup) and found ALARMING amounts.
Just to give you an idea of how outrageous these amounts are, independent research shows that probable harm to human health begins at really low levels of exposure – at only 0.1 ppb of glyphosate. Many foods were found to have over 1,000 times this amount! Well above what regulators throughout the world consider “safe”.


{See the test results and full report by Food Democracy Now! and The Detox Project}.
Here is why we all should be concerned about eating glyphosate:
- Monsanto Accused of Ghostwriting Papers on Roundup Cancer Risk
Monsanto Co. was accused in court documents of ghostwriting scientific literature that led a U.S. regulator to conclude a key chemical in its Roundup weed killer shouldn’t be classified as carcinogenic.
Lawyers suing the company on behalf of farmers and others, who claim exposure to glyphosate caused their non-Hodgkin’s lymphoma, alleged in a court filing which was partially blacked out until Tuesday that the Environmental Protection Agency “may be unaware of Monsanto’s deceptive authorship practice.”
More from Bloomberg.com: Kushners Set to Get $400 Million From Chinese Firm on Tower
The filing was made public by a federal judge in San Francisco handling the litigation. The judge said last month he’s inclined to require a retired EPA official to submit to questioning by plaintiffs’ lawyers who contend he had a “ highly suspicious ” relationship with Monsanto. The former official oversaw a committee that found insufficient evidence to conclude glyphosate causes cancer and left his job last year after his report was leaked to the press.
The plaintiff lawyers said in the filing that Monsanto’s toxicology manager and his boss were ghost writers for two of the reports, including one from 2000, that the EPA committee relied on to reach its conclusion.
More from Bloomberg.com: Why Robert Shiller Is Worried About the Trump Rally
Among the documents unsealed Tuesday was a February 2015 internal e-mail exchange at the company about how to contain costs for a research paper. The plaintiff lawyers cited it to support their claim that the EPA report is unreliable, unlike a report by an international agency that classified glyphosate as a probable carcinogen.
Monsanto Loses Bid to Keep Glyphosate Off List of Carcinogens
“A less expensive/more palatable approach” is to rely on experts only for some areas of contention, while “we ghost-write the Exposure Tox & Genetox sections,” one Monsanto employee wrote to another.
- Monsanto attempt to block glyphosate from California cancer list tossed by judge
A California state court has dismissed a legal challenge by multinational agribusiness firm Monsanto that seeks to bar the state from adding glyphosate, the lead ingredient in the company’s Roundup herbicide, to a list of cancer-causing chemicals.
On March 10, Fresno County Superior Court Judge Kristi Culver Kapetan ruled against Monsanto’s challenge to a provision of Proposition 65, a California voter initiative passed in 1986 that requires the state’s governor to publicize a list of chemicals known to cause cancer.
The California Office of Environmental Health Health Hazard Assessment proposed to add glyphosate to the Proposition 65 list after the World Health Organization’s International Agency for Research on Cancer (IARC) classified the chemical as a probable human carcinogen in 2015.
“The law requires that certain substances identified by the International Agency for Research on Cancer (IARC) be listed as known to cause cancer under Proposition 65,” the state agency said in September 2015.
Glyphosate is a key ingredient of Monsanto’s flagship weedkiller well-known under the trade name ‘Roundup.’ It is one of the most heavily used herbicides in the world and is designed to go along with genetically-modified “Roundup Ready” crops, also produced by Monsanto.
Monsanto argued that adding glyphosate to the state list based on the World Health Organization’s decision was unconstitutional.
Kapetan said none of Monsanto’s challenges to the state provision were viable. In dismissing the case, she wrote that “there does not appear to be any chance that Monsanto or [its co-plaintiffs] can amend their complaints to state valid claims under any of the theories they can rely upon.”
Hot Diggity Doge

The DOGE OF WAR
D8rgRZjcBPLAhvmUazYXxCZasueoEmP7VGUnleash the Power of the DOGE OF WAR
Please Donate to RLM
In This Doge Eat Doge World
Secure Private Alternative To Skype
Tox: Client Side only as of 4/15/2016
Jitsi:
Dump Skype – Piss Off The NSA
Silent Weapons for Quiet Wars
- The people know that they have created this farce and financed it with their own taxes (consent), but they would rather knuckle under than be the hypocrite. Factor VI – Cattle Those who will not use their brains are no better off than those who have no brains, and so this mindless school of jelly-fish, father, mother, son, and daughter, become useful beasts of burden or trainers of the same.
- Mr. Rothschild’s Energy Discovery
What Mr. Rothschild [2] had discovered was the basic principle of power, influence, and control over people as applied to economics. That principle is “when you assume the appearance of power, people soon give it to you.”
Listen How
The Law of War
General Orders No. 100: The Lieber Code
INSTRUCTIONS FOR THE GOVERNMENT OF ARMIES OF THE UNITED STATES IN THE FIELD
Where Not Throwing Oppression Off, You Live Either Under an Occupation or by Conquest.
The Choice and Responsibility are Yours. United We Strike
Behind The Woodshed for that practical education & hard but necessary dose of reality.
Spread The Word Behind The Woodshed.
(^_^)







![[Most Recent Charts from www.kitco.com]](https://www.kitconet.com/charts/metals/gold/t24_au_en_usoz_4.gif)